Information security now!
The topics of this week's review include phishing messages in the name of Ajovarma, potential data leak risks in Oracle cloud services for organisations, and Traficom’s updated guideline on security assessment and approval processes for information systems.

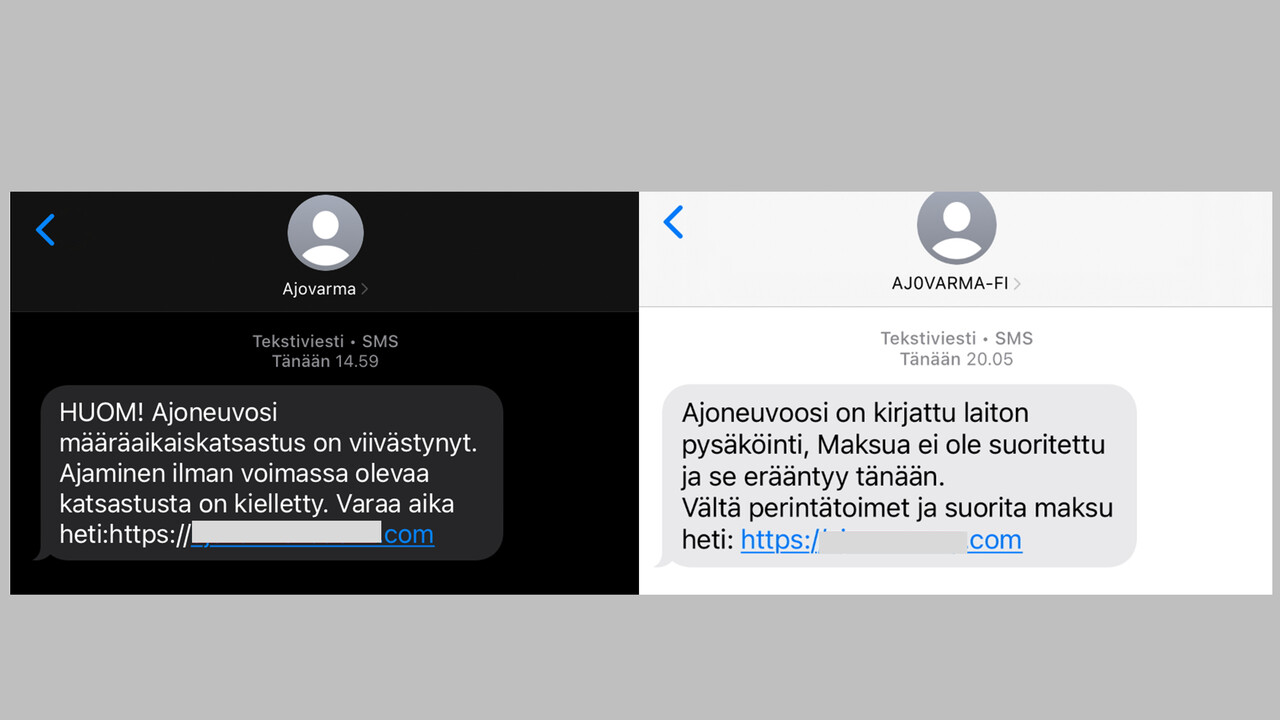
Phishing via text messages in the name of Ajovarma
The NCSC-FI has received several reports about phishing messages being sent in the name of Ajovarma. Do not open suspicious links or enter your login credentials on websites whose authenticity you cannot fully verify.
Phishing messages impersonating Ajovarma have been sent to recipients via text message. The messages claim that the recipient’s vehicle inspection is overdue or that a parking fine has not been paid. The credibility of the scam messages is reinforced by sender names resembling Ajovarma, and the victim is pressured into taking swift action by being told that driving an uninspected vehicle is illegal or that a payment is due today.
Potential Oracle data leak may pose risks to organisations
In March, allegations emerged in public regarding a data breach in Oracle’s cloud service. According to these claims, a significant amount of information had been stolen from the system. Oracle denied that any breach had taken place in the Oracle Cloud service. However, inconsistencies in the claims and in the samples of stolen data presented by the attacker have also raised doubts about the credibility of the breach allegations.
Nevertheless, the case has raised suspicions of a data leak in an older Oracle service. Last week, the United States Cybersecurity and Infrastructure Security Agency (CISA) published guidance related to a possible security incident in an outdated Oracle cloud environment. Although the scope and impact of the event have not been confirmed, CISA emphasises that any potential leak of login credentials could pose significant risks to both organisations and individual users.
Particularly concerning is the hardcoding of login credentials—such as passwords, authentication tokens, and encryption keys—into system scripts and automation tools, making them difficult to detect and vulnerable to long-term exploitation. Attackers can use such credentials, for example, to move within networks, conduct phishing operations, or sell access on criminal forums.
CISA recommends the following measures:
- Review and reset passwords and hardcoded credentials
- Implement phishing-resistant multi-factor authentication (MFA)
- Monitor for suspicious login activity
- Use strong, unique passwords and provide user training on recognising phishing attempts
Updated guideline on security assessment and approval processes for information systems
The Finnish Transport and Communications Agency Traficom has issued an updated guideline on the information security assessment and approval processes for information systems. It replaces the previously published guideline. The guideline is intended for authorities and companies that need to process nationally or internationally classified information in electronic form.
The main changes in the revised guideline focus on a more comprehensive description of the approval process lifecycle, enhanced descriptions of process phases and a broader treatment of special cases related to the handling of internationally classified information.
The NCSA function of the NCSC-FI provides guidance on matters related to assessment and approval. It is also recommended to notify the NCSA of any upcoming assessment needs. Contact us as soon as the need for an assessment or approval has been identified. This enables us to better prepare and to initiate the process quickly.
Email: ncsa (at) traficom.fi
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI.
- Instructions for victims of data leaks (External link)
Recognise online scams and protect yourself from them
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 17–24 April 2025). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.