On this page you can find information on matters such as to whom the NIS2 Directive applies and what kinds of requirements it imposes.
To whom do the obligations apply?
The regulation applies to critical sectors of society. The organisations governed by the regulatory framework are either essential or important depending on their size, sector and criticality.
Which authorities are responsible for the supervision and guidance of different sectors?
The supervisory authorities responsible for different sectors monitor that entities in their respective sectors comply with the law, the regulations issued under it and the statutes issued under the NIS 2 Directive, meaning the implementing acts adopted by the Commission.
The supervisory authorities and their sectors of responsibility are listed below.
What obligations does the regulatory framework impose?
Registering for a list of entities
Supervisory authorities maintain a list of entities in the sector they supervise.
For this purpose, an entity must provide the relevant supervisory authority with the following information:
- entity’s name, current contact details and IP ranges
- sector and subsector as referred to in an Annex to the NIS 2 Directive
- whether the entity meets the definition of an essential entity
- a list of EU countries where the entity provides services that fall within the scope of the NIS 2 Directive
- participation in a voluntary cybersecurity information-sharing arrangement.
Any changes in the information must be reported without delay and, in any event, within two weeks of the date of the change.
Compliance with the cyber security risk management obligations
An entity must have in place an up-to-date cybersecurity risk management procedure to protect communications networks and information systems and their physical environments from incidents and their impacts.
Entities must take proportionate technical, operational and organisational measures in accordance with the cybersecurity risk management procedure to manage the risks posed to the security of communications networks and information systems and to prevent or minimise the adverse impact of incidents.
The cybersecurity risk management procedure and the management measures based on it must take into account and maintain up to date at least the following:
- cybersecurity risk management policies and the assessment of the effectiveness of management measures;
- policies concerning the security of communications networks and information systems;
- security in communications network and information systems acquisition, development and maintenance, and the measures required for vulnerability handling and disclosure;
- the overall quality and resilience of products and services of direct suppliers and service providers in the supply chain, the management measures embedded in the products and services and the cybersecurity practices of direct suppliers and service providers;
- asset management and the identification of activities important to its security;
- human resources security and cybersecurity training;
- access control and authentication procedures;
- policies and procedures regarding the use of cryptography and, where necessary, measures for the use of secure electronic communications;
- observation and handling of incidents to restore and maintain security and reliability;
- backup management, disaster recovery, crisis management and other business continuity and, if necessary, the use of secure backup communications systems;
- baseline information security practices to ensure the security of operations, telecommunications, hardware, software and datasets; and
- measures to ensure the security of the physical environment and facilities of communications networks and information systems and the necessary resources.
Risk management measures must be proportionate to the nature and scope of operations, the reasonably foreseeable direct impact of an entity’s incident, the susceptibility to risks of the entity’s communications networks and information systems, the likelihood and severity of incidents and the costs of and the state-of-the-art of the measures, taking into account the technical possibilities available to prevent threats.
For more information, see Traficom’s recommendation on cybersecurity risk management measures (External link), for example. The recommendation is targeted at the authorities supervising entities, but it also supports NIS 2 entities in planning their risk management measures. Supervisory authorities can issue more detailed technical regulations regarding risk management in their respective sectors.
The recommendation includes examples of the implementation of cybersecurity risk management measures, authentication methods and links to the most commonly used standards, frameworks and tools. However, the recommendation does not propose the application of a specific standard or framework.
The entities listed below must also take into account the European Commission Implementing Regulation (EU) 2024/2690 (External link) specifying the content of risk management obligations under the NIS 2 Directive and the definition of a significant incident.
- DNS service providers
- top-level domain (TLD) name registries
- cloud computing service providers
- data centre service providers
- content delivery network providers
- managed service providers
- managed security service providers
- providers of online marketplaces
- providers of online search engines
- providers of social networking services platforms
- trust service providers
Obligation to notify significant incidents
A significant incident means an incident that has caused or is capable of causing severe operational disruption of services or financial losses for the entity concerned or an incident that has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage.
An incident means an event compromising the availability, authenticity, integrity or confidentiality of stored, transmitted or processed data or of the services offered by, or accessible via, communications networks and information systems.
An entity within the scope of the NIS 2 Directive must notify the supervisory authority of a significant incident affecting its service without delay.
The notification obligation involves three phases: the entity must submit to the supervisory authority an early warning within 24 hours of detecting the incident and an incident notification within 72 hours of detecting the incident. Once the incident is over, the entity must submit to the supervisory authority a final report.
When you notify a significant incident, the NIS 2 incident notification instructs you to provide the necessary information.

An entity must notify the users of its services of any significant incidents without delay if the significant incident is likely to disturb the provision of its services.
The entities listed below must also take into account the European Commission Implementing Regulation (EU) 2024/2690 (External link) specifying the thresholds of a significant incident as referred to in the NIS 2 Directive.
- DNS service providers
- top-level domain (TLD) name registries
- cloud computing service providers
- data centre service providers
- content delivery network providers
- managed service providers
- managed security service providers
- providers of online marketplaces
- providers of online search engines
- providers of social networking services platforms
- trust service providers
All notifications are also notified to the CSIRT at the NCSC-FI.
A person submitting a notification may request the CSIRT for help in handling the incident and submit more detailed information about the case to the CSIRT in confidence.
Penalty fees
Administrative fines are imposed by a sanctions board based on a proposal by the supervisory authority. The fine is payable to the State.
The maximum amount of an administrative fine imposed on an essential entity is EUR 10,000,000 or 2 per cent of the entity’s total worldwide annual turnover in the preceding financial year, whichever is higher. The maximum amount of an administrative fine imposed on an entity other than an essential entity is EUR 7,000,000 or 1.4 per cent of the entity’s total worldwide annual turnover in the preceding financial year, whichever is higher.
Voluntary notifications to the NCSC-FI at Traficom
All businesses and organisations can report to the NCSC-FI at Traficom any actual or attempted information security incidents they experience, such as phishing or denial-of-service attacks.
We encourage notifications even if the case does not involve a significant incident as referred to in the NIS 2 Directive, because notifications enable the NCSC-FI to help victims in the technical investigation of information security violations. The NCSC-FI also uses the information it receives to maintain national situational awareness of cybersecurity and to provide general information about cybersecurity. All notifications are processed in confidence.
Begin filling in the form below by selecting whether you are reporting an issue as an individual or as a representative of an organisation. You can also leave an anonymous tip. The form will guide you through and give you advice on the most common information security incidents.
NCSC-FI's services
How to use the Cybermeter to prepare for the cybersecurity risk management requirements?
The recommendation on cybersecurity risk management measures for NIS supervisory authorities includes links to the Cybermeter provided by the NCSC-FI at Traficom. The Cybermeter is a set of indicators based on categorised best practices for the periodic assessment, development and reporting of cybersecurity maturity level. The purpose of the links to the Cybermeter is to promote the application of the recommendation, interaction among stakeholders and the improvement of cybersecurity also at national level.
The links provided in connection with the measures in the recommendation lead to sections and objectives that contain various good practices to choose from. In future, various links that are even more specific can be created at the practical level so that it will be possible to take account of matters such as sector-specific special features and threat profiles that affect the capabilities needed for protection against cyber threats and ensuring the continuity of operations. The Cybermeter tool can be also be adapted to an organisation's own needs.

How to use the NCSC-FI’s situational awareness products?
The NCSC-FI at Traficom provides various services to support organisations covered by the NIS Directive in maintaining and improving their information security.
The NCSC-FI produces a variety of situational awareness products for organisations. The products provide their users with up-to-date information about events and phenomena affecting cybersecurity.
The NCSC-FI uses mailing lists to distribute situational awareness products and sector-specific information security notices on topical matters, for example.
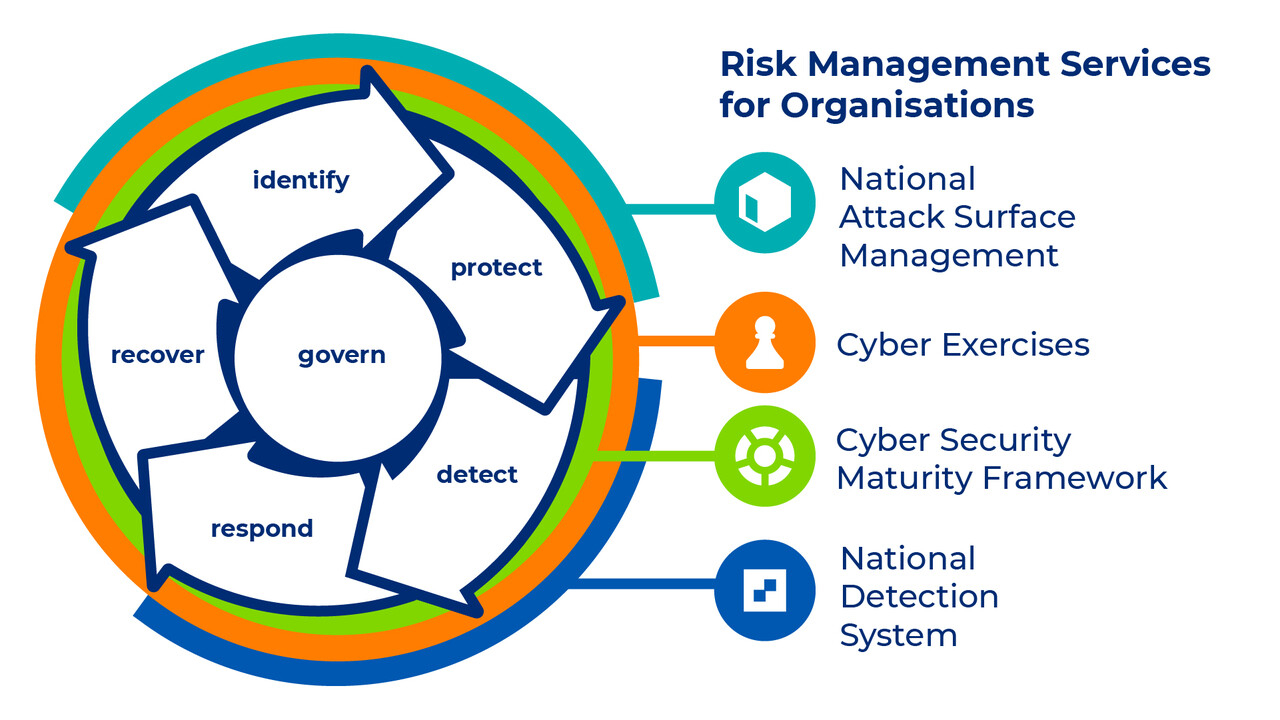
What kinds of roles do other authorities play in cybersecurity and data protection matters? How and when to contact them?
Police
The police acts as the competent authority in preventing and investigating information network crimes and bringing them to the consideration of charges. Most of the information network crimes are investigated by the local police. All police departments have units specialising in the processing and analysis of digital evidence. The national Police Customer Service Helpline operates at the number +358 295 419 800 (weekdays from 8:00 to 16:15) or by email at neuvontapalvelu@poliisi.fi.
The National Bureau of Investigation (NBI) is a national unit of the Finnish Police operating across Finland. The NBI includes the Cybercrime Centre, a unit specialising in the pre-trial investigation of information network crimes. It mainly investigates extensive information network crimes targeted at information network environments that have social significance and act as a precedent. In order to file a police report, fill in the electronic police report form or notify the local police about the case.
You can file a police report either online or by visiting your local police station. There is also an online tip-off form you can use to report even the smallest cyber disruptions or observations that do not meet the statutory definition of an offence. An organisation is responsible for the first response to an information security event it has detected as well as the restrictive and other measures. For an investigation by the police, the organisation should make sure that the evidence is secured for a potential criminal investigation later. In practice, this means documenting the targets, events, measures and times as accurately as possible. Recovering the systems and telecommunications logs as extensively and comprehensively as possible is of primary importance. Log data must be stored and kept unchanged and in their original format.
Office of the Data Protection Ombudsman
The Data Protection Ombudsman is a national supervisory authority that monitors compliance with data protection legislation. The duties of the Data Protection Ombudsman include monitoring compliance with the data protection legislation and other laws on the processing of personal data, promoting awareness of the risks, rules, protective measures, obligations and rights related to the processing of personal data, drawing up reports, carrying out inspections and imposing administrative sanctions for violations of the General Data Protection Regulation. If the authorities referred to in the Cybersecurity Act become aware of a personal data breach in connection with a notification of a significant incident or their other supervisory duties, they are required to pass on the information to the Data Protection Ombudsman. Such notifications by supervisory authorities do not remove the controller’s obligation to report a personal data breach.