Information security now!
This week, we report on current scams and provide the NCSC-FI’s perspective on the denial-of-service attacks observed over the past week.
Topics covered in this week’s review
- .fi domain does not guarantee safety – don’t fall for scam websites
- Organisational invoicing details of interest to criminals
- Hacktivist denial-of-service attacks have had limited impact on Finnish websites
- County and municipal elections culminate this weekend
- Obligations under the NIS 2 Directive entered into force 8 April 2025

.fi domain does not guarantee safety – don’t fall for scam websites
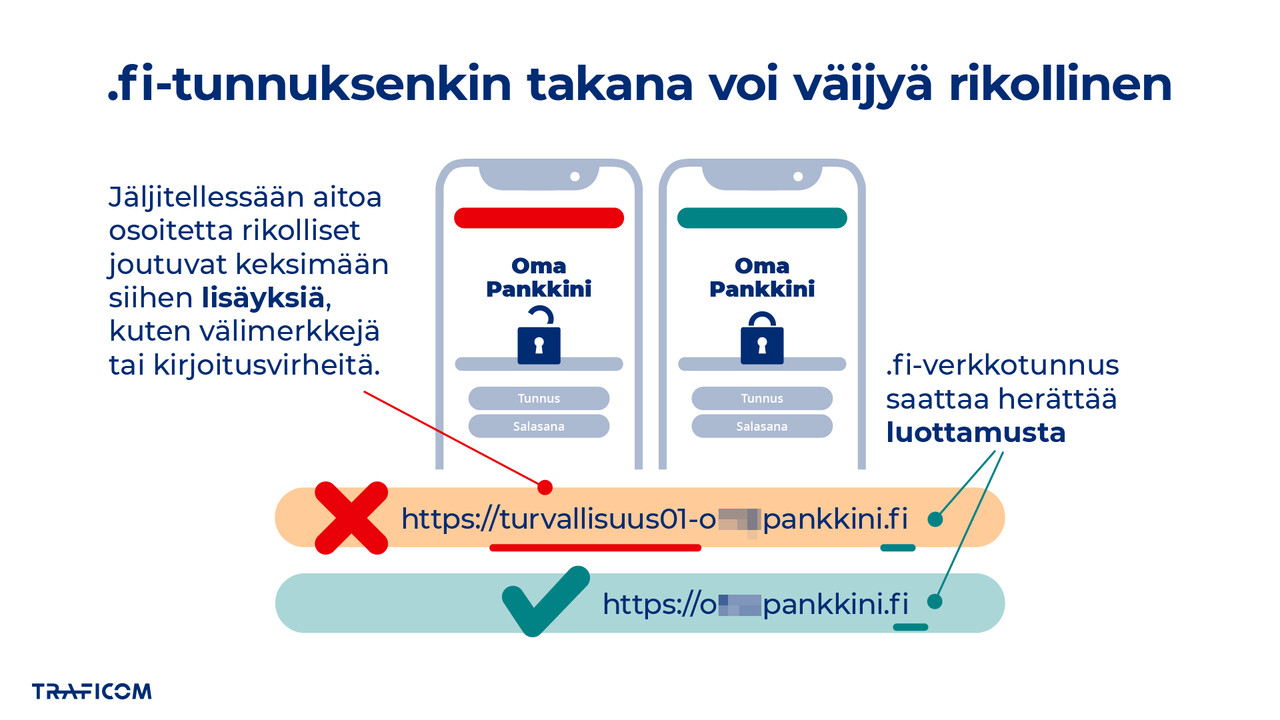
Finnish websites with a .fi domain are often perceived as secure. However, from time to time, cases emerge where this trust has been exploited. The NCSC-FI has recently again received reports of phishing websites registered with a .fi domain name, used by criminals to deceive users into disclosing sensitive information, such as online banking credentials.
These scam websites have recently been observed impersonating organisations such as the Finnish Patent and Registration Office, the Finnish Tax Administration’s Incomes Register and various banks. These are not the official websites of these organisations but fraudulent sites designed to resemble them, using the .fi domain to foster a false sense of trust.
It is therefore important to remember that a .fi domain alone is not a guarantee of trustworthiness. Always check the full web address carefully. Since a specific domain name can only be registered by one party, criminals often register addresses that closely resemble legitimate ones, but with slight alterations, such as misspellings, added characters, or hyphens.
The appearance and content of a website can also indicate fraud. For example, grammatical errors, a disorganised layout, or links leading to suspicious destinations are warning signs. If a site redirects to a service that does not match the domain name, it is advisable to close the browser immediately.
The NCSC-FI is actively working to combat phishing. As the Finnish Transport and Communications Agency Traficom manages .fi domains, the centre often receives requests to take down scam websites or to prevent their registration entirely. However, blocking domain names involves broader legal and societal considerations.
Domain names play a central role in the dissemination of information and the realisation of freedom of expression. This means that domain registration cannot be pre-emptively prevented, nor can sites be taken down without careful case-by-case assessment. Blocking is only done temporarily and based on individual consideration, if other measures prove ineffective. Experts at the NCSC-FI investigate every site to be blocked and ensure it truly poses a significant cybersecurity threat—such as a publicly accessible site harvesting banking credentials.
Organisational invoicing details of interest to criminals
The NCSC-FI has recently received reports of phishing messages aimed at committing invoice fraud. These phishing attempts have been sent under the guise of organisations such as Traficom and wellbeing services counties. In the messages, a criminal impersonating the organisation’s financial manager attempts to persuade the recipient to send the organisation’s outstanding invoices in PDF format.

Once they gain access to these invoices, the criminals may alter them in order to redirect payments to bank accounts under their control. In addition to falsifying genuine invoices, they may also attempt to request payment for entirely fabricated invoices.
Similar fraud campaigns have been observed and discussed before. For example, see Weekly Review 43/2024 (External link).
Hacktivist denial-of-service attacks have had limited impact on Finnish websites
This past week, there have been news reports about denial-of-service (DoS) attacks carried out by the pro-Russian hacktivist group NoName057(16) targeting Finnish websites. Over the week, the group has directed DoS attacks at websites belonging to organisations in the energy, finance and logistics sectors. Websites of political parties have also been targeted. Despite the attacks continuing throughout the week, the overall impact has remained moderate—even though several of the targeted organisations had not previously been affected by NoName's activities.

A central part of NoName057(16)’s modus operandi is to dramatically exaggerate the impact of their attacks in their own communications. Disruptions lasting only a few minutes are reported as “site shutdowns.” In addition to overstating attack effects, the group’s messaging often includes disinformation, such as exaggerated or implausible claims about Finnish politicians or Finland’s foreign policy. These extreme narratives that often seem unbelievable to Finns suggest the intended audience may lie outside Finland.
While denial-of-service attacks rarely have significant long-term effects, their potential impact should not be underestimated. For example, in the autumn of 2024, DoS attacks targeting the finance sector caused prolonged disruptions.
Today, DoS attacks by pro-Russian hacktivists have become a familiar nuisance in Finland and across the Western world. As a result, preparations for such attacks are well established. Although the attacks themselves cannot be entirely prevented, their effects can be mitigated. Technical solutions for identifying and blocking attack traffic are a crucial part of preparedness for any organisation providing services online. As part of this readiness, organisations should also prepare to communicate clearly about any disruptions. To support this, the NCSC-FI published a crisis communication guide earlier this spring.
County and municipal elections culminate this weekend
Advance voting concluded on Tuesday, and attention now turns to the official election day on Sunday, 13 April. Authorities' long-standing efforts to ensure the security of the elections are also approaching their final stage for this election cycle. The smooth and secure implementation of national elections is a good example of an undertaking involving many different authorities. At best, voters do not even notice the preparations and measures taken.
Finland has always been able to hold reliable elections, and the Finnish election system is stable and secure. The voting conducted with ballot papers cannot be easily interfered with by attacks on information systems. Similarly, the reliability of counting the votes by hand cannot be influenced by cyber attacks.
It is, however, worth reminding once again that during the election weekend we may see denial-of-service (DoS) attacks, which often attract media attention. In some cases, such attacks could cause temporary disruptions to election-related services, such as the results service. However, DoS attacks cannot affect the actual election results or their reliability. Preparations have been made for potential DoS attacks in connection with the elections. Authorities share information about any related observations promptly and openly, and service providers are also well informed and alert to the situation. In general, it can be noted that Finland’s preparedness for various types of threats remains at a high level.
You can read our guidelines and articles related to election cybersecurity on our election webpage (External link)
Obligations under the NIS 2 Directive entered into force 8 April 2025
Finnish Parliament has passed the government proposal for a national Cybersecurity Act to implement the EU Cybersecurity Directive (NIS 2 Directive). The aim of the NIS2 Directive is to ensure a common level of cyber security across the European Union. Obligations under the NIS 2 Directive entered into force in Finland on 8 Month 2025
The NIS 2 Directive and the related national Cybersecurity Act impose risk management obligations on sectors critical to society, aimed at enhancing cybersecurity, along with a duty to report significant incidents. The Act lists minimum measures that all entities must implement to manage the cybersecurity risks posed to their operations. Entities are also required to notify the relevant supervisory authority of significant information security incidents. Moreover, entities within the scope of the NIS 2 regulatory framework must also register for a list of entities maintained by the authority supervising their sector.
The Cybersecurity Act entails new risk management and reporting obligations for many sectors. The obligations enter into force gradually. One the first steps is registering for a list of entities by 8 May 2025.
More information
March Cyber Weather report published
The March edition of Cyber Weather appears slightly sunnier compared to February, although data breaches, exploitation of vulnerabilities, scams, and phishing campaigns have continued—fuelled by constantly evolving tactics. In terms of sector-specific developments, the first quarter of the year saw an increase in incident reports across many sectors compared to the final quarter of 2024.
The March Cyber Weather report also examined the evolution of cybersecurity regulation from several perspectives: the Cybersecurity Act (NIS 2), the Gigabit Infrastructure Act, the proposed prioritisation of electronic communication in official government operations, and progress on the Cyber Resilience Act. The report additionally provided an overview of the state of cybercrime in Europe.
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
What to do if you get scammed
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking codes or got hold of your payment card information.
- File a police report. You can file a police report online. (External link) (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Guidance for victims of a data leak (External link)
Learn how to detect and protect yourself against online scams
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 04–10 April 2025). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.