End the contact
If you suspect that you have fallen victim to a romance scam, stop contacting the scammer immediately.
This week we cover topics such as romance fraud and how to prepare for disruption in the cyber world.

On this Valentine's Day, the NCSC-FI would like to remind you about romance scams
So-called romance or love scams are among the best known forms of online fraud. Scammers are ready to ruthlessly appeal to the victim's emotions and are committed to prolonging the deception over long periods of time.
In a nutshell, the scammer tries to pose as a fictitious person and approach the victim online, for example through a dating app or social media.
As the two become acquainted, the scammer may start asking the victim for help, for example to send money. A long-standing emotional attachment may cloud the victim's judgement and they may not perceive the situation as deceptive. In reality, the money sent ends up in the hands of a criminal.

Falling victim to a romance scam can cause shame. It is worth remembering that scammers manipulate and exploit the vulnerability and benevolence of the victim in a systematic and often prolonged way, and it is not the victim's fault that they fall victim to a romance scam. There is no point in hiding it, as being open and reporting it can help both the victim and others to avoid similar experiences.Falling victim to a romance scam can cause shame. It is worth remembering that scammers manipulate and exploit the vulnerability and benevolence of the victim in a systematic and often prolonged way, and it is not the victim's fault that they fall victim to a romance scam. There is no point in hiding it, as being open and reporting it can help both the victim and others to avoid similar experiences.
If you suspect that you have fallen victim to a romance scam, stop contacting the scammer immediately.
If you gave your bank details or transferred money to a scammer, contact your bank immediately and let them know.
Record the communication with the scammer, for example with screenshots.
Report the matter to the police. You can report a crime electronically, for example.
Nettideittiturva, for example, provides support for people who have experienced romance scams. The joint project of the Sosped Foundation and Maria Akatemia ry develops and produces nationwide low-threshold, face-to-face support for people (victims and loved ones) who have experienced romance fraud in order to help them deal with the situation.
Victim Support Finland also provides help and information on romance scams
It's also a good idea to tell your family and friends.
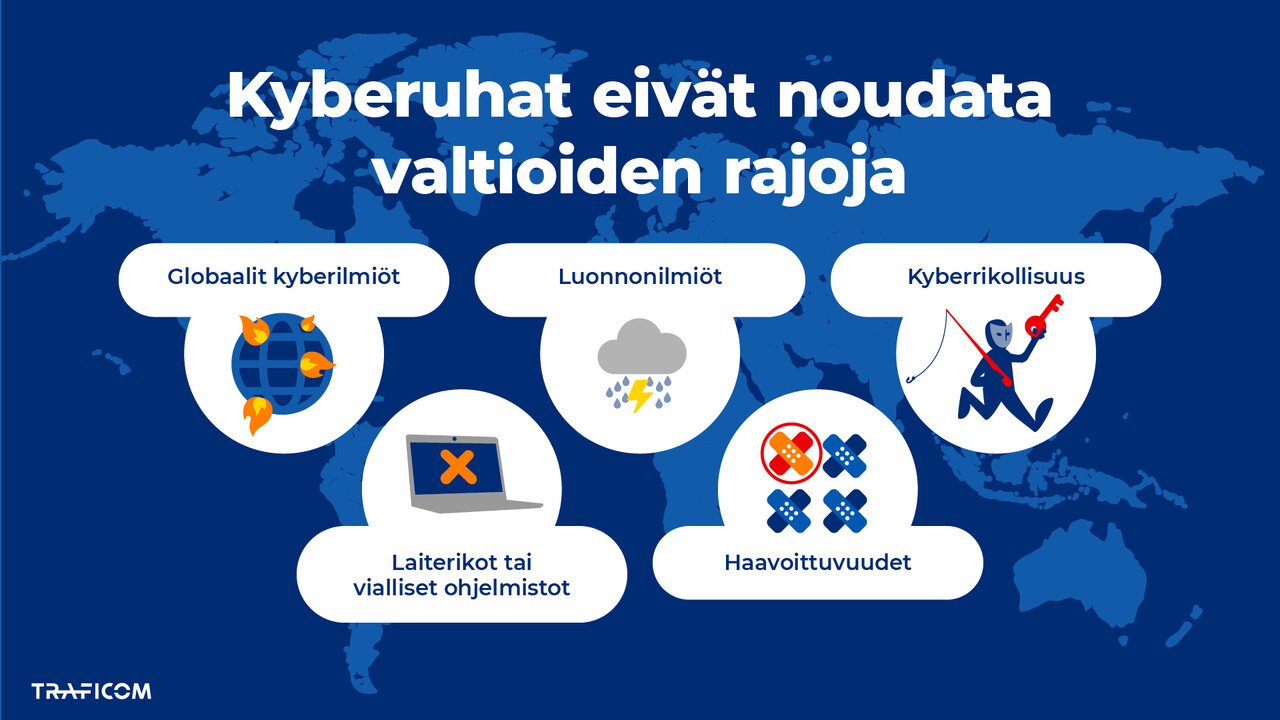
In today's fast-paced information age, guesswork, assumptions and "snap judgements" often take on too much value in the face of disruptive situations. It is important to be able to communicate about incidents in a timely manner, but also with facts, whether the facts are what is known, what is not known or by openly stating what is currently the "understanding" of the current state of affairs. The cyber world experiences a wide variety of incidents on a daily basis, and the vast majority of them are not in any way "cyber" in a malicious form. Very often, a faulty or broken component, human error, a natural phenomenon or, in certain situations, and unexplained "crossover bit" is at the root of the problem.
Over the past week, both 72-hour Home Emergency Food Supply Day and 112 Day have been celebrated. It is up to each one of us to do our part to be prepared, whether at home or at work. What are our contingency plans? What if phones are not working? How can I contact others? What if my debit card doesn't work? Is there cash or possibly another kind of bankcard available? Similar issues are being considered in business risk management: What if software critical from an operating point of view stops working? What is the alternative? What if a key person is not available at a critical time? Can someone else do the same thing or are the instructions at a level where anyone can fill in with sufficient skills?
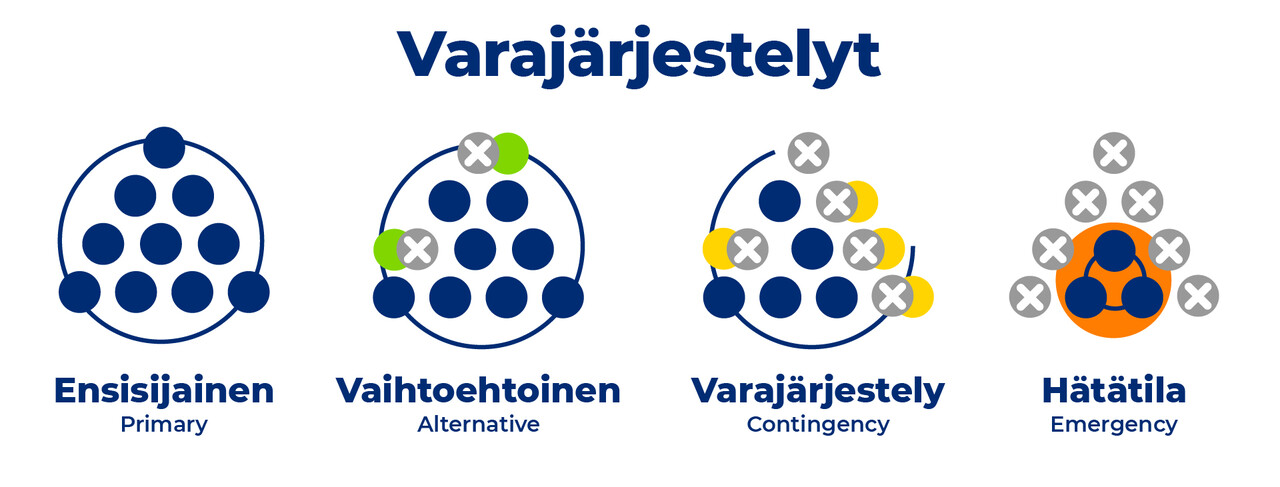
Many of you will at some time have heard the Scout motto: “Ole valmiina - var redo - be prepared”. Those two words sum up preparedness in the cyber world, too. Another rule of thumb that provides a little more guidance is the old PACE – Primary, Alternative, Contingency and Emergency – often repeated, especially in government. This rule of thumb makes it easy to review backup arrangements. Primary and alternative arrangements allow all operations to be handled almost identically, contingency arrangements require prioritisation of services to be used or activities to be performed, and emergency arrangements prioritise the most critical aspects of operations and accept, for example, longer delays. Although it is said that “well begun is half done”, preparedness must also be practised and resources must be allocated to it. This is the only way to build resilience to different kinds of incidents.
This year, the NCSC-FI is bringing a variety of content to the Disobey event on 14–15 February, including technical CTF challenges and expert mentoring.
At the event, visitors will have the opportunity to learn about the NCSC-FI’s activities and receive mentoring from cybersecurity experts Mentoring offers support with issues such as career development or cybersecurity skills development.
In addition, technical CTF puzzles created by experts from the NCSC-FI will challenge visitors' wit and technical skills. Can you solve our challenges requiring diverse skills?
You can find us at the Traficom stand in Disobey's Community Village on both days of the event.
Acquaint yourself with the event programme: Disobey Community Village. (External link)

Traficom's NCSC-FI contributes to the security of all national elections by providing support to election authorities in exchanging cyber threat information, building situational awareness and protecting against cybersecurity threats. In addition to its cooperation with the authorities, the NCSC-FI has also distributed information to political parties and publishes election-related guidelines and articles on its website.
Regional and municipal elections will be held on 13 April 2025. According to the Association of Finnish Municipalities’ candidate analysis (PDF) (External link), there were more than 35,000 candidates in the last municipal elections. Now that regional elections are being held on the same day, there could be even more candidates. Within the framework of its mission, the NCSC-FI wants to support the election work of parties and candidates by providing up-to-date and practical guidance and support on issues such as the secure use of smart devices and securing social media accounts. That's why we are publishing a bi-weekly election cybersecurity newsletter, which anyone can subscribe to at their email address if they wish.
A new year of cyber weather, and with it new phenomena! The January 2025 Cyber Weather Report published 12 cybersecurity phenomena of long-term relevance, which the NCSC-FI is specifically monitoring this year. Cyber Weather will also cover the top 5 quarterly threats.
This time, Cyber Weather highlights vulnerabilities, both in the cases that affected January's weather, in long-term monitoring of phenomena and as one of the top 5 threats.
In 2023 and 2024, the National Coordination Centre of Traficom's NCSC-FI provided financial support totalling around EUR 2 million to 50 micro and small and medium-sized enterprises for the implementation of modern information and cybersecurity solutions and innovation. According to the impact assessment, the direct impact of the aid on business cybersecurity is significant, and it is also expected to improve national cybersecurity through B2B customer relationships and supply chains.
Most of the companies that received funding are active in the ICT, health, digital services and digital infrastructure sectors. The objectives of the projects were often related to the protection of customer data, business secrets and other sensitive information, as well as the security of communications. Around half of the companies also sought to improve the security of the technology in their equipment and production environment.
Around 80% of the respondents estimated that the project had improved their ability to respond to threats in the short term, increased security awareness in the organisation and enabled them to develop security in the context of the overall architecture.
The fact that 82% of the respondents reported that the project helped them identify new development needs related to information security serves as a good prediction of the long-term impacts of the financial support.
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
Recognise online scams and protect yourself from them
CVE: CVE-2025-22467, CVE-2024-38657, CVE-2024-10644
CVSS: 9.9
What: Critical vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure
Product: Ivanti Connect Secure and Ivanti Policy Secure
Repair: Updates to newer versions.
Read more: Vulnerability report 6/2025 (External link) (in Finnish)
This is the weekly review of the National Cyber Security Centre Finland (reporting period 07–13 February 2025). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.