Information security now!
This week, we'll be covering, among other things, the latest in M365 phishing and how end-of-year sales and the abundant sending of parcels are getting criminals moving.

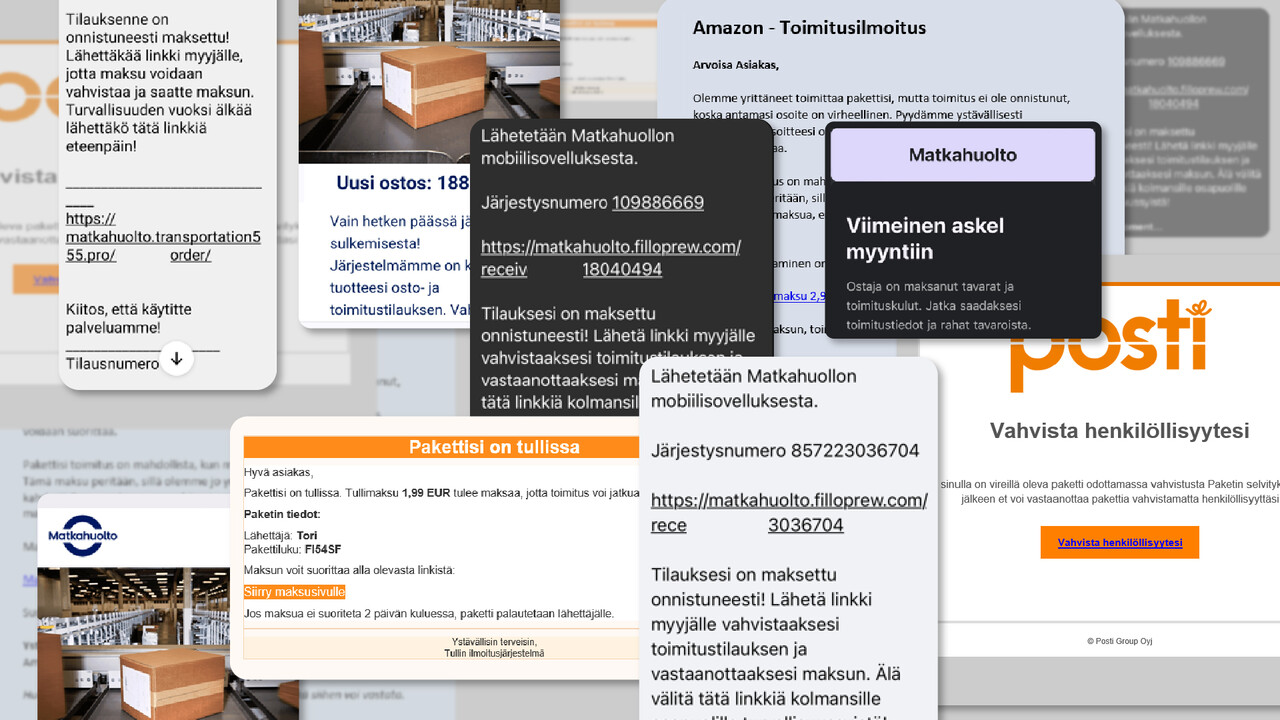
End-of-year sales and abundant parcels get criminals moving too
November marks the start of the end-of-year sales and the Christmas shopping season. Online stores are bustling and there are clearly more parcels in circulation than normal. Cyber criminals know this too and are keen to exploit the topicality of these themes in their crimes. By tempting you with unbelievable offers and scaring you with stories of lost parcels, criminals try to get their hands on the wallets of honest citizens. So be on the lookout again this season! Is this staggering offer real or just a scam? Is the message from the post office or courier service about the parcel I ordered, or is someone trying to trick me?
The most common scams of the season include parcel-themed scam messages, bogus online stores and subscription traps. The key to avoiding scams is to keep a cool head when it comes to both tempting discounts and scary alerts. Moderation is the key and it's a good idea to discuss any dubious situations with someone close to you.
If you find yourself a victim of a crime, for example by giving your online banking credentials to a phishing site or buying products from an online store that doesn't inspire confidence after you've made a purchase, the most important thing is to contact your bank quickly and report the incident to the police.
Phishing for M365 credentials via Dropbox – be extra vigilant!
Dropbox-themed M365 account phishing is currently very active. The phishing proceeds as follows:
1. An email from someone you know: You receive an email from an acquaintance saying they are sharing a file via Dropbox because they failed to send a PDF file as an email attachment.
2. Dropbox email message: Next you receive an email from Dropbox. The message contains a link that takes you to Dropbox. When you click on these links, a page opens asking you for your email address and password. The user IDs entered on the site end up in the hands of criminals.
How does the attack proceed?
The user IDs and passwords are used by criminals to access emails in your M365 account and to search for information such as invoices and emails related to money transfers. The criminals try to alter the content of these emails and forward them to the victim's contacts through the victim's email address. For example, the victim's contacts may receive an invoice from the victim's email address that appears to be legitimate, with only the account number for the payment changed.
Using the victim’s M365 account, the attacker may attempt to hijack the victim’s Dropbox account or even create a new account in the victim's name. A compromised Dropbox account can be used to send new phishing messages, which can be spread to perhaps thousands of people in the user's contacts.
Here's what to do – be alert!
The National Cyber Security Centre (NCSC-FI) urges you to be particularly careful when opening attachments and links. Always check carefully which service you are entering your credentials for, especially on the login pages. On a real Microsoft site, the address always starts with https://login.microsoftonline.com/, and the site certificate is issued by Microsoft; any other alternative is inherently dubious and potentially harmful.
Don't suffer alone – immediately report if you've been scammed!
If you suspect that you entered your credentials on a rogue phishing site, contact your organisation's IT support or data security staff immediately.
The NCSC-FI encourages users to not be afraid to report any phishing messages or sites. Early reporting can prevent new victims from being scammed and help prevent the spread of attacks.
A report can be filed directly at NCSC-FI's website (External link)or in free form by email to cert@traficom.fi.
Read more: What to do in the event of Microsoft365 account compromise
Digital skimming – tips to protect online stores
Digital skimming is an attack method used by cyber criminals to install malicious code into an online store's payment systems. This code is designed to steal users' payment card details and other information provided during the payment process, such as personal data and address details.
This is a major threat that can go unnoticed for long periods of time, causing significant financial and reputational damage to websites and their customers. We published an Information Security Now! article from which an online store administrator can pick up tips on how to detect, prevent and deal with digital skimming after it has occurred.
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking codes or got hold of your payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI.
- Instructions for victims of data leaks (External link)
Learn how to detect and protect yourself against online scams
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 22 November–28 November 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.