Information security now!
M365 credentials are now being actively phished for, in particular through the Dropbox service. Please be careful with files you receive from Dropbox.

Criminals using Dropbox to phish for M365 credentials
Since July, Traficom's National Cyber Security Centre has been notified of around 60 M365 account breaches. There have also been reports of cases where an attacker, having committed a data breach, has remained to monitor the hacked account.
In particular, Dropbox-themed M365 account phishing seems to be active now. In the phishing email, a PDF file is sent to the recipient via Dropbox. In the PDF file that is shared, there is a link to a website that asks for M365 credentials. Passwords entered on this site end up in the hands of a criminal. Once inside the M365 account, the attacker hijacks the user's existing Dropbox account, if any, or creates a new account in the user's name. A hacked Dropbox account can be used to send phishing messages. Phishing messages may be sent to thousands of hacked user account contacts.
While restoring an M365 account is reasonably easy for an organisation, restoring a Dropbox account is more difficult. The organisation has no access to the account management, no knowledge of the password set by the attacker or the method of multi-factor authentication.
Prevent, report, react
- NCSC-FI urges all Microsoft 365 customers to communicate internally about the phishing messages in circulation.
- Forced implementation of multi-factor authentication is an effective protection against phishing.
- We recommend that you check internally within your organisation whether you need to have the right to install different applications directly on your Microsoft 365 subscription.
- An application called eM Client has also been used in data breaches. The application itself is not harmful, but its features have also been used for illegal purposes. The installation of the application may indicate that a data breach has occurred.
- If you suspect you have received a phishing message, report it to your organisation's IT support. You can also report (External link) the phishing message and its links to the NCSC-FI. The NCSC-FI will examine the link in the message and report malicious links to the site administrator.
August cyber weather dry
The cyber weather in August continued to be calmer than usual. The reported cases highlighted scams and phishing targeting citizens.
A ray of sunshine in the cyber weather was brought by Traficom's revised regulation on telecoms data security. The revised regulation (External link) takes into account the evolution of communications networks and services and responds to new security threats.
The autumn is also a busy one for regulation, with the EU AI regulation having come into force in early August and the national requirements of the NIS2 Directive coming into force in early October.
This week in our long-term cyber security phenomenon watch, we focused on data security for cloud services. Speed, cost efficiency and flexibility are the main attractions of cloud services. Unfortunately, cyber attacks are also moving to cloud environments.
Find out about the brand new cyber weather report (External link)
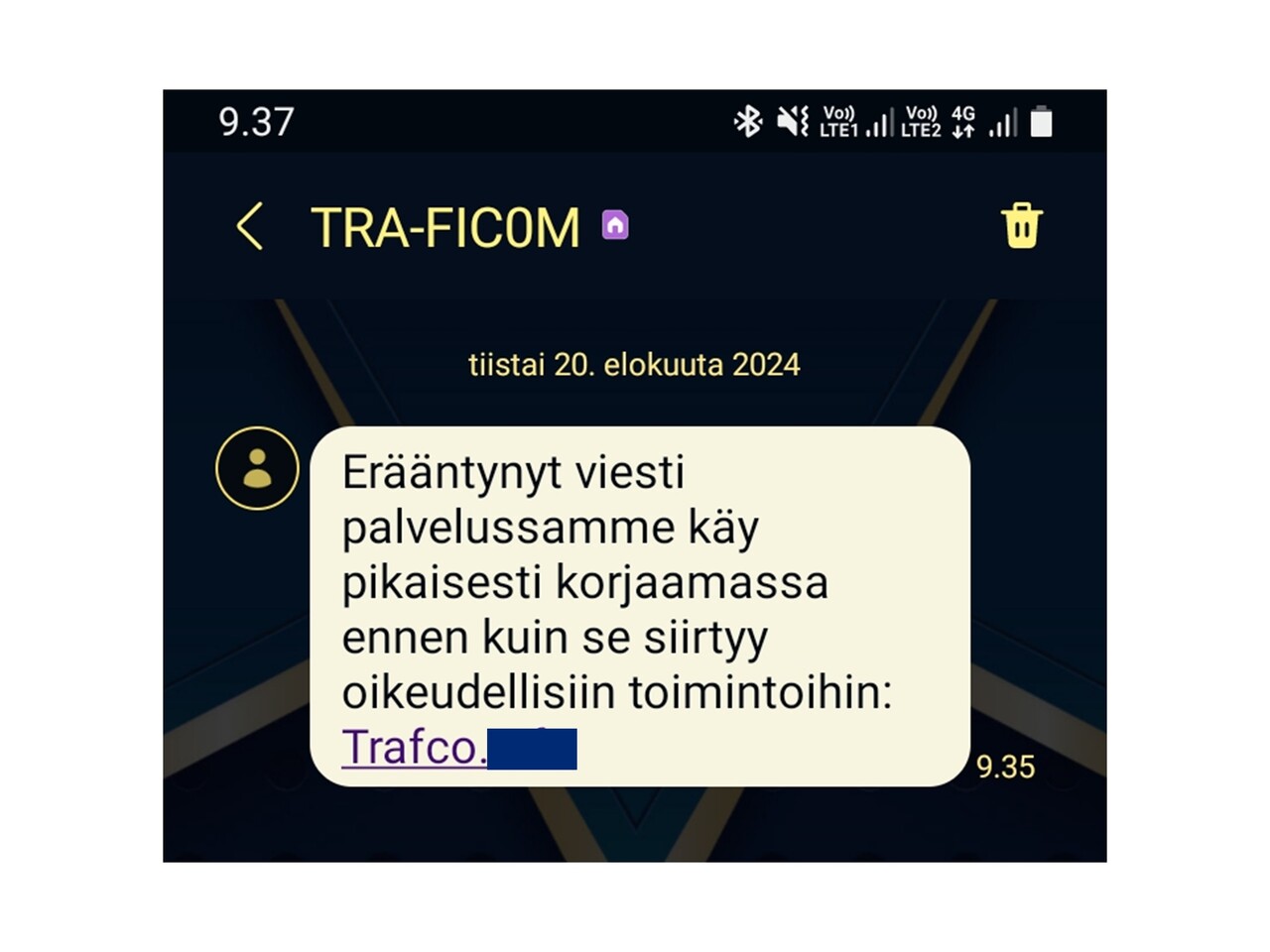
Scam messages again in the name of Traficom
The Transport and Communications Agency (Traficom) is warning about (External link)different scam messages being sent in its name. These are phishing messages that try to get you to click on a link in the message and give your bank account details to criminals.
Do the following:
- Do not click on links in emails or text messages.
- Do not go to services via links or search engine results, but type the full address of the website in the address bar.
- Save the web addresses of the services that matter most to you in your browser bookmarks or favourites, where you can safely access them.
- If you have mistakenly handed over your credit card details or online banking credentials, you may have been a victim of fraud. First contact your own bank and then report the crime to the police. Attempts at fraud should also be reported.
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
What to do if you get scammed
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking codes or got hold of your payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Instructions for victims of data leaks (External link)
Learn how to detect and protect yourself against online scams
Vulnerabilities
CVE: CVE-2024-40766
CVSS: CVSS 9.3
What: SonicWall SSLVPN vulnerability being actively exploited (External link)
Product: SonicWall SSLVPN
Repair: Update to the latest version
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (reporting period 6–12 September 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.