Information security now!
This week, we talk about the importance of cyber security exercises and information security during holiday periods, among other topics.
Topics covered in this week’s review
- Prevention of and recovery from a large-scale cyber attack practised in Europe
- A lesson in information influence activities
- Scammers phishing for bank credentials with text messages centred around fines
- Do not forget about information security awareness during the holiday season
- Traficom’s guide on how to securely erase data on storage media

Prevention of and recovery from a large-scale cyber attack practised in Europe
The European Union Agency for Cybersecurity (ENISA) organised the pan-European Cyber Europe 2024 exercise on 19–20 June. This was the seventh edition of the exercise, which is held on even-numbered years. This year’s exercise involved simulating a massive cyber attack on the European energy sector and information society carried out jointly by advanced persistent threats (ATP) and criminal actors. The scenario was designed to be realistic, as the simulation was based on real detected threats against critical infrastructure.
The participants were provided with a wide variety of different technical and operative inputs, giving both new and experienced employees an opportunity to practise their tasks. For organisations, the exercise provided an opportunity to train staff on technical investigation, incident management, crisis communications and operational continuity.
The participants of the Cyber Europe 2024 exercise consisted of the cyber security authorities of 30 European countries, several European Union agencies, actors and networks and over 1,000 professionals in different fields representing their own organisations. Participating in the exercise also allowed organisations to develop their national and international cooperation and information exchange. Finland’s participation in the exercise was coordinated by the NCSC-FI. In total, nearly ten Finnish private sector and government organisations took part in the exercise at different levels.
“From a national perspective, it was great to see the participating organisations demonstrate their capacity to operate under pressure during a demanding incident. There was an open and confidential culture of information exchange between the participating organisations, which is excellent in terms of societal crisis preparedness,” says Information Security Specialist Otto-Petteri Jämsén.
An After Action Report (AAR) on the exercise compiled by ENISA will be published on ENISA’s website at the end of the year.

A lesson in information influence activities
The latest episode of the Futucast podcast features Head of Communications Jussi Toivanen from the NCSC-FI and Head Of Communications Päivi Tampere from the Prime Minister’s Office discussing information influence activities with host Isak Rautio.
According to Toivanen, the key component of information influence activities is a story that elicits strong reactions. While information influence activities are not really a new phenomenon, their effectiveness is strengthened by advancing technologies that make communication more immediate and impactful.
Kuuntele jakso täältä (External link)
Lue lisää: Kyberturvallisuuskeskuksen artikkeli informaatiovaikuttamisesta (External link)
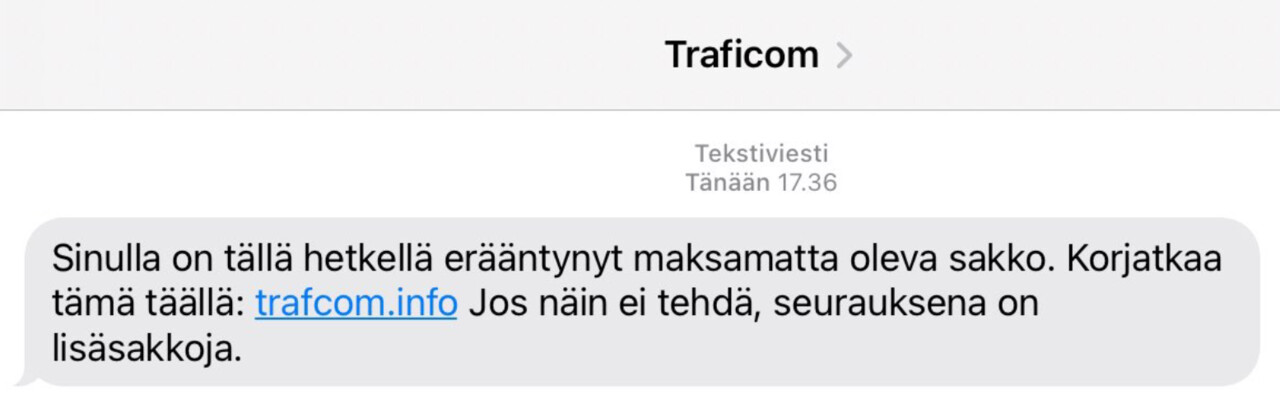
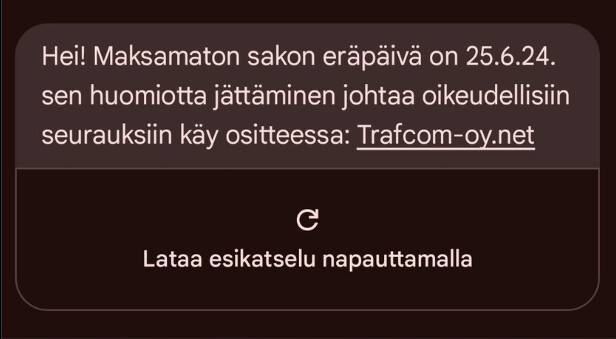
Scammers phishing for bank credentials with text messages centred around fines
Over the past week, we have received dozens of reports of scam messages sent in the name of the Finnish Transport and Communications Agency Traficom. The scam messages claim that the recipient has an unpaid fine that is past due. The message is a phishing message designed to get the recipient to click on the included link and hand their bank credentials over to criminals.
If you have received a message like this, delete it without clicking the included link. If you have mistakenly provided the scammers with your credit card information or bank credentials, immediately contact your bank. After that, file a police report.
Do not forget about information security awareness during the holiday season
Various types of scams and phishing attacks usually increase at the start of holiday seasons. The fact that organisations operate with fewer resources during holiday seasons can tempt criminals to try their luck at invoice fraud, for example.
During the spring and early summer, the NCSC-FI has received reports of various types of CEO fraud attempts, fake invoices, websites phishing for bank credentials and M365 account information and phishing sites under the names of authorities, among others. All of these have the potential to cause significant damage to organisations. Luckily, they can also be avoided with the right practices and personnel training.
Tips for the holiday season:
- Provide training on good information security practices to summer employees as well.
- Holidays can affect the availability of resources, but do not let this be a reason for deviating from secure work practices.
- Stay even more vigilant than normal during the holiday season, as the numbers of various information security incidents can increase during the holidays.
- Remember to take care of the information security of network devices and keep them updated during the holidays as well.
Last summer, we compiled a set of instructions concerning various invoicing scams. The start of the holiday season is the perfect time to refresh your memory and implement best practices:
Traficom’s guide on how to securely erase data on storage media
Traficom has published a new guide for organisations’ risk management personnel on how to securely erase protected data on and reuse digital storage media. The guide describes the most common preconditions for the reliable and verifiable erasure of data on and reuse of storage media.
Read more here (in Finnish)
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
FOLLOW THESE INSTRUCTIONS IF YOU HAVE BEEN SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or gotten hold of your payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Guide for the victims of data leaks (External link)
Learn how to detect and protect yourself against online scams
Vulnerabilities
CVE: CVE-2024-5806
CVSS: 9.1
What: A critical vulnerability that can lead to authentication bypass.
Product: MOVEit Transfer
Fix: Follow the manufacturer’s instructions to protect yourself until an official patch is released.
CVE: Several
CVSS: 8.8
What: Chrome browser updates
Product: Google Chrome
Fix: Update Chrome to the latest version.
CVE: CVE-2024-38369
CVSS: 10.0
What: WordPress InstaWP Connect Plugin
Product: WordPress
Fix: Update the product to the latest version.
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 20 July–27 July 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.