Information security now!
This week, our topics include CEO fraud and how supply chain attacks have increased in recent years. We also look back at the previous month with the May Cyber Weather report.

Topics covered in this week’s review
- CEO fraud season has begun again, stay vigilant
- May Cyber Weather 2024
- The NIS2 Directive addresses the security of procurements and supply chains as well
- Request for comments about Finland’s Cyber Security Strategy
- Sign up for Kybermittari-day on 14 August
CEO fraud season has begun again, stay vigilant
CEO fraud attempts typically take place during holiday periods. In recent years, the numbers of CEO fraud attempts reported to the NCSC-FI have been highest during the summer.
Criminals can attempt many different types of scams by impersonating a CEO. Examples include sending messages to employees asking them to purchase gift cards or pay invoices. The fraudsters will often claim that the matter is extremely urgent, thus justifying the bypassing of normal processes. The fraudsters may also claim that the CEO is currently in a place where they cannot talk or attending a meeting. CEO fraud attempts are primarily carried out via email, but there have also been cases of the fraudsters contacting potential victims by phone.
How CEO and invoice fraud is carried out
Most recently reported scam messages have started with an inquiry such as “Hi, can you do me a favour?” or “Hi, can you make a bank transfer today?”, followed by a request to transfer money, usually abroad. Another common approach has been to go straight to the point with a single message: “What is our bank balance? We need to make a payment of EUR XX,XXX.XX. Can we do it today?”
Any sudden changes in invoicing information should be viewed with suspicion. Fraudulent invoices can also come from the email addresses of previously trustworthy persons or organisations if criminals have managed to hijack their email accounts.
Who can be targeted by CEO fraud
CEO fraudsters often target organisations and companies whose payment transaction processes and related procedures are not as established as those of larger companies. This increases the chance of success of the fraud attempt.
Recently, CEO fraudsters have been targeting various non-governmental organisations in particular. In most cases, the fraudster has done some groundwork and identified the key personnel of the organisation in advance. After this, the fraudster has impersonated a person with some authority in the organisation and sent a message about a payment transaction to the person responsible for the organisation’s finances.
In addition to CEOs, criminals may also impersonate financial, payroll or HR personnel. During the spring, there have also been several cases of fraudsters impersonating company employees in an attempt to get payroll to change their bank account number on short notice.
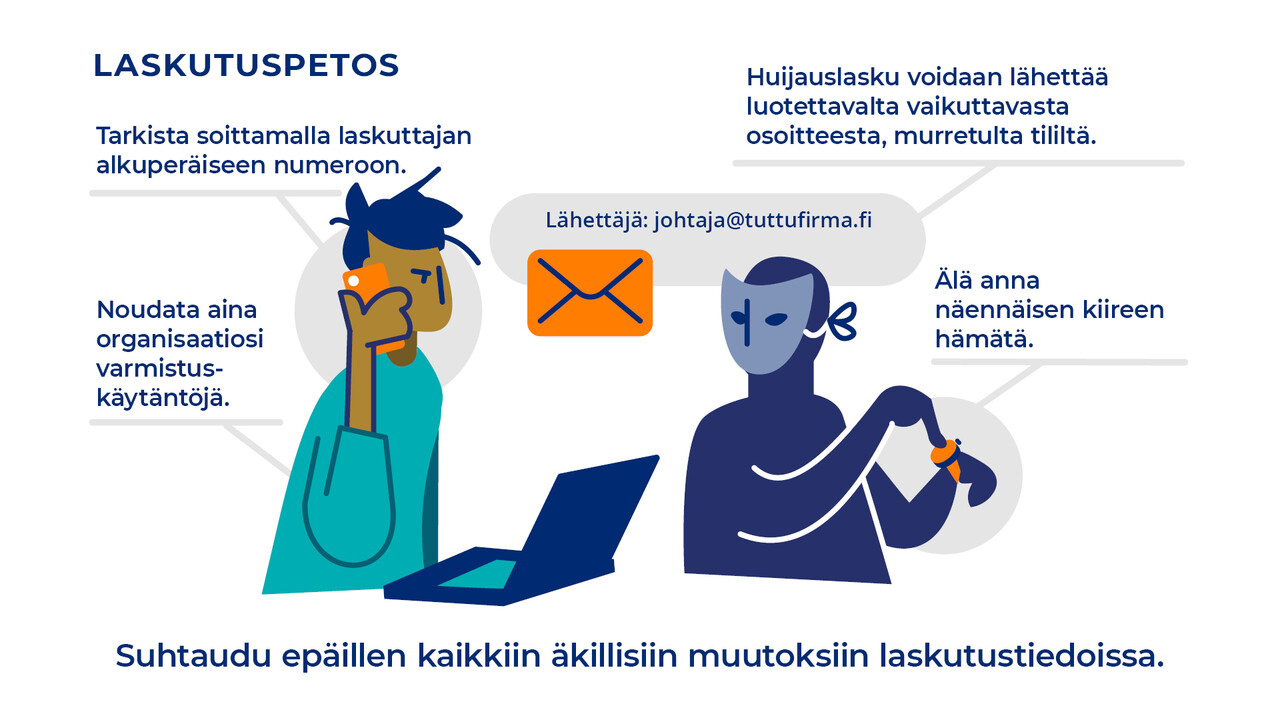
How to protect against CEO and invoice fraud
The most effective way of protecting your organisation from CEO and invoice fraud is to be suspicious of any payment requests that you receive via email and always verify the request by phone or using the original contact information of the issuer if you are unsure about it. It is important for organisations to remind summer employees – and even senior employees from time to time – of the organisation’s correct procedure for processing incoming invoices.
Read more about how to protect against CEO and invoice fraud:
Summer means a peak in invoicing scams – how to protect yourself against fraud (External link)
Guidance for civil society:
Kyberuhkien lieventäminen rajallisilla resursseilla (‘Mitigating Cyber Threats with Limited Resources’, article in Finnish) (External link)
May Cyber Weather 2024
The Cyber Weather remained gloomy in May, with the skies darkened by public announcements of several data breaches and leaks in particular. Scams and phishing also made for some stormy weather.
The most notable Cyber Weather events in May included the City of Helsinki data breach and the unauthorised searches performed on registers maintained by public authorities, which were found to be the result of a data breach suffered by a client organisation. As regards phishing, there was a new wave of attacks utilising the Microsoft Planner scheduling and task management software for Microsoft 365 account compromise. The attacks involved using Microsoft Planner to share a PDF file that contains a link to a phishing site.
Read more (in Finnish): May Cyber Weather 2024 (External link)
The NIS2 Directive addresses the security of procurements and supply chains as well
Supply chain attacks, which have grown increasingly common in recent years, can affect large numbers of suppliers and customers at the same time. This has also been taken into account in the NIS2 Directive, which imposes obligations related to the security of procurements and supply chains.
Be sure to check out our new article on the security of procurements and the most common cyber attacks targeting supply chains. The article also presents some administrative and technical methods to support risk management.
Request for comments about Finland’s Cyber Security Strategy
The NIS2 Directive (link to a Finnish page) (External link)entering into effect in October 2024 obligates EU Member States to update their national cyber security strategies. The updating of Finland’s Cyber Security Strategy is also based on the current Government Programme, which states that the strategy will be updated to correspond to the changed operating environment.
The updated strategy has been prepared by an intersectoral Government working group with input from nearly a hundred public and private sector, science community and NGO operators. Comments are currently also being requested for a draft Security Strategy for Society.
THE OBJECTIVES AND DEVELOPMENT MEASURES OF THE STRATEGY
Finland’s Cyber Security Strategy extends up to 2035 and includes strategic objectives and common development measures organised under four pillars:
I: Know-how, technology and RDI – A competent, innovative and exploratory cyber ecosystem
II: Preparedness – Strong societal cyber resilience and operating reliability
III: Cooperation – A robust national and international cooperation model
IV: Response and countermeasures – Timely response to threats and secure sovereignty
Details of the request for comments
Lausuntopyyntö Suomen kyberturvallisuusstrategiasta (External link)
Vastausaika päättyy 9.8.2024
Lausuntopyynnön diaarinumero: VN/36693/2023
Lausuntopyyntö luonnoksesta Yhteiskunnan turvallisuusstrategiaksi 2024 (External link) (YTS2024)
Lausuntopyynnön diaarinumero: VN/12457/2021
Vastausaika päättyy 9.9.2024
Kybermittari-day on 14 August – sign up now!

Kybermittari is a tool that helps companies and organisations assess and develop their own cyber security. If you need help for managing your organisation’s cyber security or are already a user of Kybermittari, be sure to sign up for the Kybermittari-päivä event! The event will be held in Kumpula, Helsinki, in the afternoon of 14 August 2024.
At Kybermittari-päivä, you will learn about users’ experiences of using our service as part of cyber security management. You will also get to discuss and influence the future of the service. In addition to this, the event programme includes perspectives on the cyber threat environment and necessary capabilities as well as discussions about compliance and risk management. During the latter part of the afternoon, you will also get to contribute to the discussion and network with other participants.
Kybermittari-päivä will be held in Helsinki at the Kumpula campus, address Dynamicum, Erik Palménin aukio 1. Be sure to sign up soon, as the number of participants is limited to approximately 70. We would primarily like to see only one person sign up per organisation.
Up-to-date event information is available on the Kybermittari-päivä page (in Finnish) (External link).
Sign up using the registration form (in Finnish) (External link).
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
FOLLOW THESE INSTRUCTIONS IF YOU HAVE BEEN SCAMMED:
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or gotten hold of your payment card information.
- File a police report. You can file a police report online. (External link)
You can also report the incident to the NCSC-FI. (External link)
Learn how to detect and protect yourself against online scams
Vulnerabilities
CVE: CVE-2024-30299
CVSS: 10
What: Adobe have released security updates patching several critical vulnerabilities in their software products.
Product: Adobe FrameMaker Publishing, Adobe Commerce and Magento platforms.
Fix: Install Adobe’s security updates for the vulnerable software without delay in accordance with the provided instructions.
Further information: Vulnerability bulletin 16/2024 (External link)
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 7–13 June 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.