Information security now!
This week, we report on domain names falling into the wrong hands, which has also been covered in the media. We explain the difference between a website and a domain name, and advise on how to properly manage and administer a domain name. Other topics include new ways of spreading the Lumma Stealer malware, the Digital Security Week and the start of Cyber Security Month, and protecting your SMS Sender ID.
Tällä viikolla katsauksessa käsiteltäviä asioita

Domain name expiry causes debate
In the past week, the National Cyber Security Centre (NCSC-FI) has received reports of expired domain names that have been re-registered by an opportunistic actor who has set up websites that mimic the previous ones. We published an Information Security Now! article on taking care of domain names.
If a domain name is allowed to expire, someone else can re-register it. Under outside control, the domain name is no longer yours and anything from casino ads to adult entertainment can appear on the site. When creating a domain name, consider carefully whether it could cause damage to you or the brand you manage if you ever give up the domain name. You should plan ahead and consider whether you can give up your domain name or whether you should keep it permanently.
It is therefore important to remember to keep your domain names valid. A good way is to make a note in your calendar one month before the next expiry date.
Don't take a domain name just for the summer! – domain names are valuable assets (External link)
A new way to spread data-stealing malware
The Lumma Stealer malware has been spreading in a new way since August. We have seen how victims have been lured to a website under the pretext of authentication to execute a malicious command in Windows, after which Lumma Stealer is installed on their computers. Information stolen by malware can be sold on or exploited as it is.
According to NCSC-FI, the malware has been spreading in the following ways:
- In a pop-up advertisement on a website
- By manipulating search results, for example by searching for software or a document
- In an incoming GitHub notification by email
Regardless of the method of spreading it, the page that spreads the malware asks the victim visiting the page to authenticate themselves as a genuine user. The authentication is similar to the Captcha authentication used on other websites. When the "I'm not a robot" button is pressed, the JavaScript code on the site is activated and copies a malicious PowerShell command to the victim's clipboard. The victim is then asked to open a Windows dialogue box and paste the malicious command into the box that opens. Finally, the victim is asked to execute a command that is not fully visible to them. The command uploads the Lumma Stealer malware to the victim's computer.
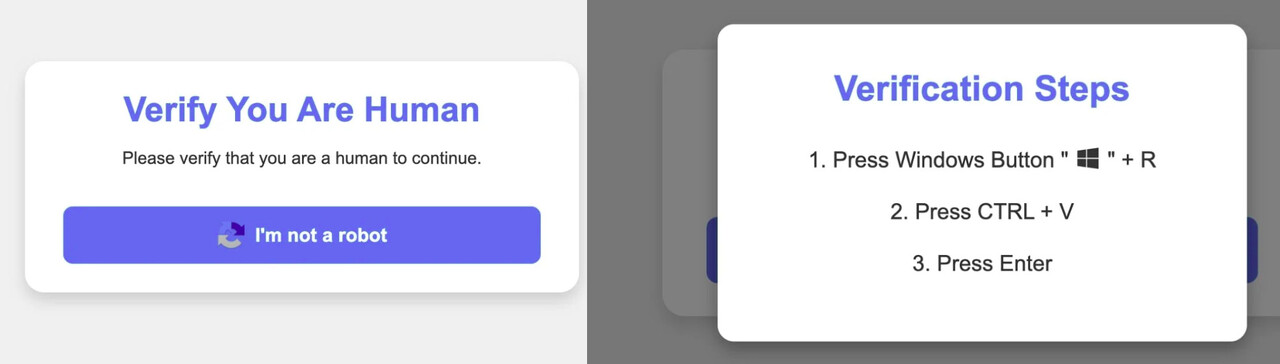
The Lumma Stealer malware steals log-in information, cookies used to authenticate to online services and browsing history from victims' web browsers. The malware is also able to steal crypto currency wallets and files found on the victim's device. Data stolen by malware, a favourite of cyber criminals, can be sold on or used as is in data breaches or phishing.
How then to avoid Lumma Stealer malware infection? Here too, traditional methods of prevention are essential. Keep all software up to date, including antivirus software. It is important for organisations to maintain up-to-date identification information in their antivirus and terminal device monitoring tools.
- The Digital Security Week and European Cyber Security Month
This week has been the traditional Digital Security Week. Hundreds of organisations from all over Finland took part in the week, which was being held by the Digital and Population Data Services Agency for the fifth time. The Digital Security Week offers concrete ways to improve cyber and digital security. During the week, participants hear from digital security experts and share tips on how to promote their own digital well-being. The NCSC-FI was also a prominent participant in the week’s events.
On Monday, our security expert, Matias Mesiä, was on hand to discuss what to do if you are a victim of online crime. On the same day, our security expert Samuli Könönen also participated in a panel on the state of cybercrime in Finland and Jarkko Saarimäki, Director General of the NCSC-FI, took part in a classic Digital Security Week panel discussing the broader state of cybersecurity in Finland.
The Digital Security Week also served as the kick-off for a wider European Cyber Security Month. This year, the theme of the month is social manipulation. The people we meet on the internet may be quite different from what they claim to be. People and identities may be fake, digitally altered or impersonate someone you know. By using different identities, criminals seek to manipulate other users and get them to act against their own interests.
Follow the campaign on social media with the hashtags #ThinkB4UClick and #CyberSecMonth.
A stop to scam messages with fake names
Cyber criminals run scams worth tens of millions of euros every year. The NCSC-FI has repeatedly warned about scams sent both in the name of Traficom and of other organisations
Thanks to co-operation between Traficom and telecommunications operators, it is now possible in Finland to protect SMS Sender ID against forgery. Organisations can protect the SMS Sender IDs they use and ensure that no one else can use the same ID in Finland. Once the Sender ID is protected and authenticated, the recipient of the message can be assured of the message’s authenticity.
Traficom has also protected its own SMS Sender ID. In total, there are already almost 200 organisations that have protected their IDs. We recommend all organisations sending SMS messages to protect their Sender ID as soon as possible.
Vulnerabilities
CVE: CVE-2024-47076, CVE-2024-47175, CVE-2024-47176, CVE-2024-47177
CVSS: 9.9
What: Vulnerabilities in the CUPS printing system enable arbitrary code execution
Product: Common UNIX Printing System
Repair: patch
About the weekly review
Tämä on Kyberturvallisuuskeskuksen viikkokatsaus (raportointijakso 27.9.-2.10.2024). Viikkokatsauksessa jaamme tietoa ajankohtaisista kyberilmiöistä. Viikkokatsaus on tarkoitettu laajalle yleisölle kyberturvallisuuden ammattilaisista tavallisiin kansalaisiin.