Information security now!
This week, we report on the state of denial-of-service (DoS) attacks, ransomware and new scams.

Topics covered in this week’s review
- Deteriorating autumn weather for DoS attacks.
- The increasingly threatening tone of ransomware
- Akira and Lockbit ransomware in the spotlight
Deteriorating autumn weather for DoS attacks
The National Cyber Security Centre (NCSC-FI) has received more active reports of DoS attacks during the past week than previously. Nordea reported that its recent disturbances were partly due to DoS attacks. So far, in other cases, the impact has been limited.
Last week, we wrote in our weekly review (External link)about the autumn DoS attack situation and the carpet bombing phenomenon that has also been observed this week. Although the situation of DoS attacks has intensified, the ordinary citizen has no reason to worry. DoS attacks are directed towards Finland on a daily basis, and some of them sometimes have an impact on the availability of services. It is up to organisations to protect themselves against such attacks. When services are affected by DoS attacks, organisations check which method the attacker used to bypass security. After that, with the right measures, the same trick will not work again.
The increasingly threatening tone of ransomware
So-called sextortion and police scams are quite common for criminals due to their ease of mass distribution. The messages are not true. Oppressive and threatening language and particularly sensitive subjects are used to try to make the victim panic and pay the ransom demanded by the blackmailer.
Now some criminals have started to put more effort into their blackmail messages. In Finland and around the world, there have been some cases where criminals have added a picture of the victim’s street in order to enhance their blackmail message. The images have been retrieved from Google Maps, for example. The contact details of the targeted people could have been obtained in many different ways, such as from old data leaks, from companies trading in data or from social media. Many people’s contact details are available through number services.
With extra effort, criminals can make their blackmail messages more credible. While seeing your home address and a photograph of your home in an extortion message is understandably frightening, it is just a devious way to intimidate the victim into paying the ransom demanded.
It is still likely that the majority of blackmail messages will be low-effort mass messages.
Akira and Lockbit ransomware in the spotlight
We published an Information Security Now! article in which we discussed Akira and Lockbit ransomware (External link). Both are globally significant criminal groups, and the use of these malicious programs has been highlighted in ransomware attacks detected in Finland. The article also discusses ways to protect against ransomware attacks, the most important of which are keeping your devices up to date and introducing multi-factor authentication for all users.
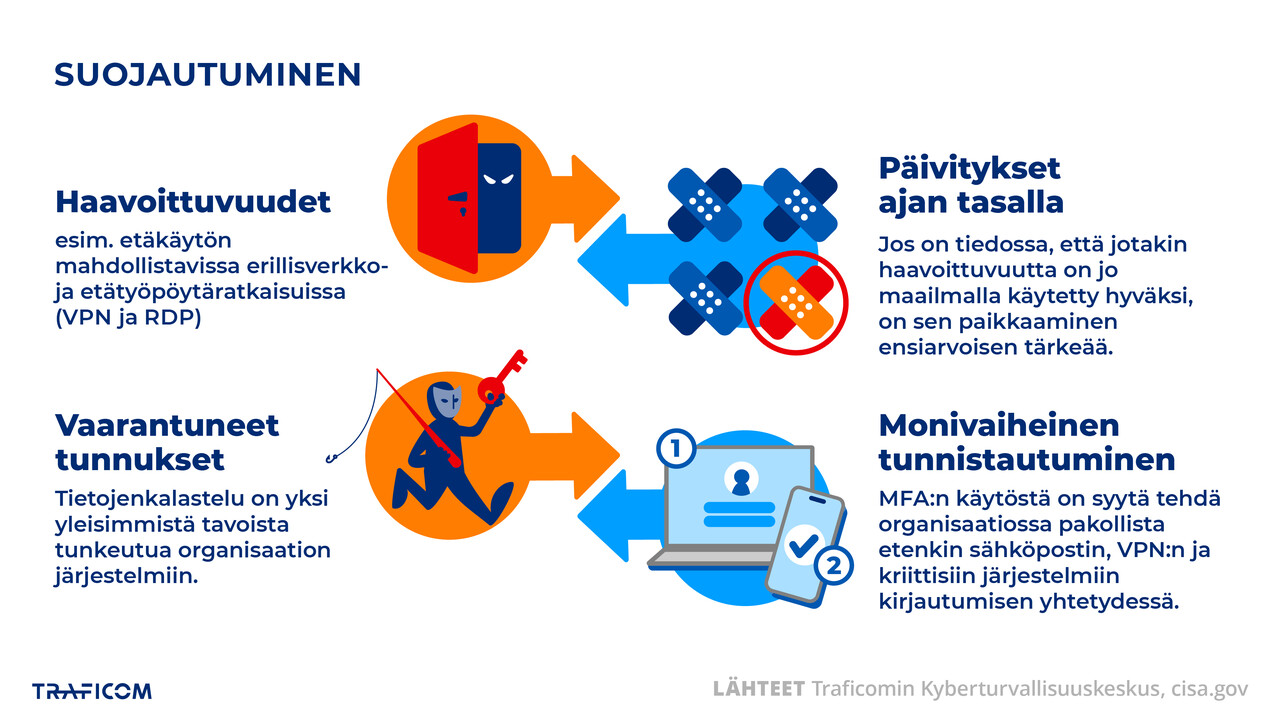
Akira has been reported to be exploiting a recent vulnerability in SonicWall SSL VPN to break into user accounts and gain access to the organisation's network. The user accounts that have been taken over have been local and no MFA has been deployed. We published a vulnerability bulletin (External link) in early September. Now is the time to update your SonicWall SSL VPN products!

Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking codes or got hold of your payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Instructions for victims of data leaks (External link)
Learn how to detect and protect yourself against online scams
Vulnerabilities
CVE: CVE-2024-42505, CVE-2024-42506, CVE-2024-42507
CVSS: 9.8
What: HPE Aruba Networking Access Points vulnerabilities
Product: HPE Aruba Networking Access Points
Repair: Update your products
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 20–26 September 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.