SERVICE: YouTube
Databreach and data leak - what are they? (In Finnish)
When you move to the YouTube website, please note that YouTube has its own cookie and privacy policies.
This week, we take a look at how organisations can map the information security of their own services and at the risk management obligation of the NIS2 Directive, among other topics.

The Australian Department of Home Affairs has confirmed to the media (External link) that they are working with Ticketmaster to understand a cyber security incident related to the company. According to public sources, the personal details of 560 million Ticketmaster customers may have been leaked in a data breach. The incident is yet another reminder of the importance of following basic cyber hygiene rules, such as not using the same passwords in multiple services.
The NCSC-FI reported on a similar incident back in 2019, when information security specialist Troy Hunt revealed a massive data leak of 773 million user records. The article also highlighted good information security practices for users of online services (article in Finnish) (External link).
When you move to the YouTube website, please note that YouTube has its own cookie and privacy policies.
Organisations can have numerous different information systems, and without automation or organised monitoring, it can be difficult to keep them all up to date and secure. It is extremely important for organisations to map their own services in order to be able to identify and understand the potential vulnerabilities and risks associated with them. Mapping also facilitates the planning and implementation of risk management measures, which significantly reduce the likelihood of security incidents.
The recommended first step in the mapping process is to list all of your organisation’s services and their details down to the version number. Based on the list, it is easy to start checking how each service is kept up to date and administered and identifying services that might need to be updated. The mapping can also reveal new systems and devices, the use of which has so far remained ‘hidden’ within the organisation. It is important to also identify the so-called crown jewels of the organisation, meaning the most important services that should always be kept up to date. These are services that the organisation should also monitor by technical means and collect and retain log data on over a sufficiently long period of time.
There are several services available on the internet that organisations can use to carry out attack surface analyses on their public IP addresses. The services allow users to discover and examine a wealth of information about resources that are publicly accessible from the internet. These include open ports, the services running on the ports and their versions. The search functionality of the services can also be used to determine whether a service of a particular IP address is affected by known vulnerabilities.
These kinds of services include:
These tools must always be used in compliance with laws, regulations and the necessary permits from the owners of the networks and/or systems.
The aforementioned services can be useful tools for company IT departments, for example. Identifying online services and making sure that only the necessary points are open to the internet can improve an organisation’s information security. Mapping services can also help organisations see what they look like from the point of view of an outsider or potential attacker.
Another useful tool that organisations can utilise in mapping their infrastructure is the DNS protocol. There are a number of services available online that organisations can use to map their domain. These services offer reports about domains based on DNS data, which include information about their subdomains, hosting services and geolocation, for example.
These kinds of services include:
A national attack surface analysis service to improve cyber security in municipalities and public sector organisations. Read more here (in Finnish) (External link).
The NCSC-FI welcomes reports of various observations and can serve as the contacting party if you notice a service belonging to some other organisation that has room for improvement in terms of information security.
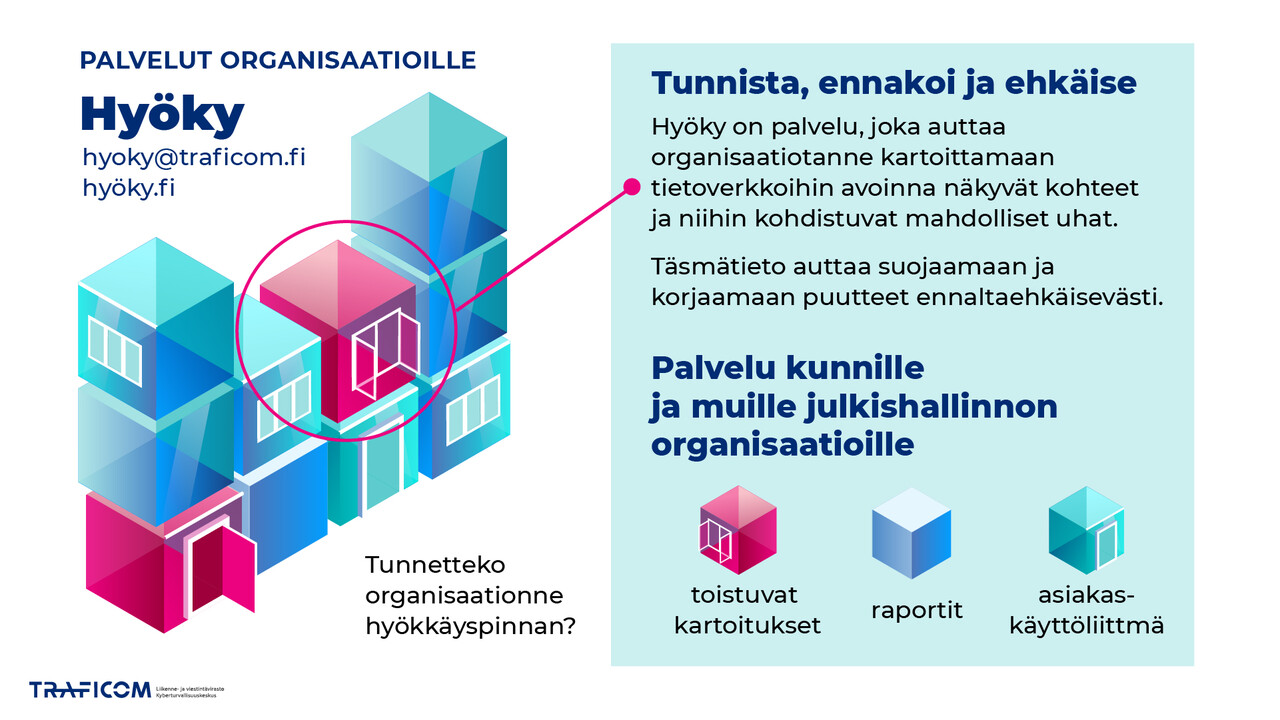
Do you know your organisation’s attack surface? Hyöky is a service that can help your organisation map targets open to the internet and the potential threats associated with them.
The NIS2 Directive lays down provisions on cyber security risk management and obligations pertaining to baseline management measures. According to the Directive, organisations must identify the risks associated with their communications networks and information systems and protect themselves against them. It is important to ensure the continuity of operations and service provision even during incidents.
Risk management is continuous, and it must adapt to changes in the operating environment. Traficom’s draft recommendation provides support for planning risk management, and the included risk management frameworks can help with systematic risk assessment and management.
Read more and master the risk management process (in Finnish) (External link)!
The ‘Kyberala murroksessa’ seminar series continues on 10 June 2024 at 12:30–14:30. How will the quantum technologies currently being developed affect cyber security? What kinds of threats, but also opportunities, does quantum computing offer in terms of the development of cyber security and threat response? How have authorities and companies prepared for the quantum age?
These are just some of the questions that will be explored in the webinar organised by Traficom’s NCSC-FI, the National Emergency Supply Agency and the Finnish Information Security Cluster. The event will examine quantum technologies in cyber security from the perspective of authorities, companies and research.
The webinar will be held on 10 June at 12:30–14:30. The event will include the publication of the Digital Pool’s new quantum report and feature speeches by SSH Fellow Suvi Lampila from SSH Communications Security Oy and Vice President Jouni Flyktman from IQM Quantum Computers.
Sign up for a free two-part introduction and application writing training webinar on the Digital Europe Programme’s cyber security calls, which will be launching in July 2024. The webinars will be held on Teams on 18 June 2024 at 13:00–15:00 and 28 June 2024 at 9:00–11:00. A more detailed invitation will be published during the week starting on 3 June.
More information and inquiries: NCC-FI@traficom.fi
How do Finnish authorities investigate and combat international cyber crime? How was the perpetrator of the Vastaamo data breach tracked down? What does the City of Helsinki data breach teach us?
Chief Adviser Kauto Huopio from the NCSC-FI joins the Futucast technology podcast to discuss how Finnish authorities prevent cyber crime perpetrated from abroad, among other topics.
Listen to the episode here (in Finnish). (External link)

In this summary, we provide information about scams reported to the NCSC-FI during the past week.
You can also report the incident to the NCSC-FI. (External link)
CVE: CVE-2024-24919
CVSS: 7.5
What: Severe vulnerability in Check Point Quantum Gateway products (page in Finnish) (External link)
Product: Check Point Quantum Gateway products
Fix: Install the patch offered by the manufacturer on vulnerable devices without delay according to the provided instructions. It is also recommended to check whether devices that used the vulnerable configuration and were accessible from the internet were breached before the installation of the patch.
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 24–30 May 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.