SERVICE: YouTube
Ethical hacker Marjana Leppäaho tells what motivates her to participate in the Hack the Networks event
When you move to the YouTube website, please note that YouTube has its own cookie and privacy policies.
This week, we talk about how important it is for organisations to invest resources in information security, as demonstrated by the recent City of Helsinki data breach, for example.

1. There are no shortcuts to good information security
2. Financial assistance for the deployment of modern cyber security solutions and innovations granted to 36 companies
3. Mitigating Cyber Threats with Limited Resources: Guidance for Civil Society published
4. Hack the Networks 2024 taking place this weekend
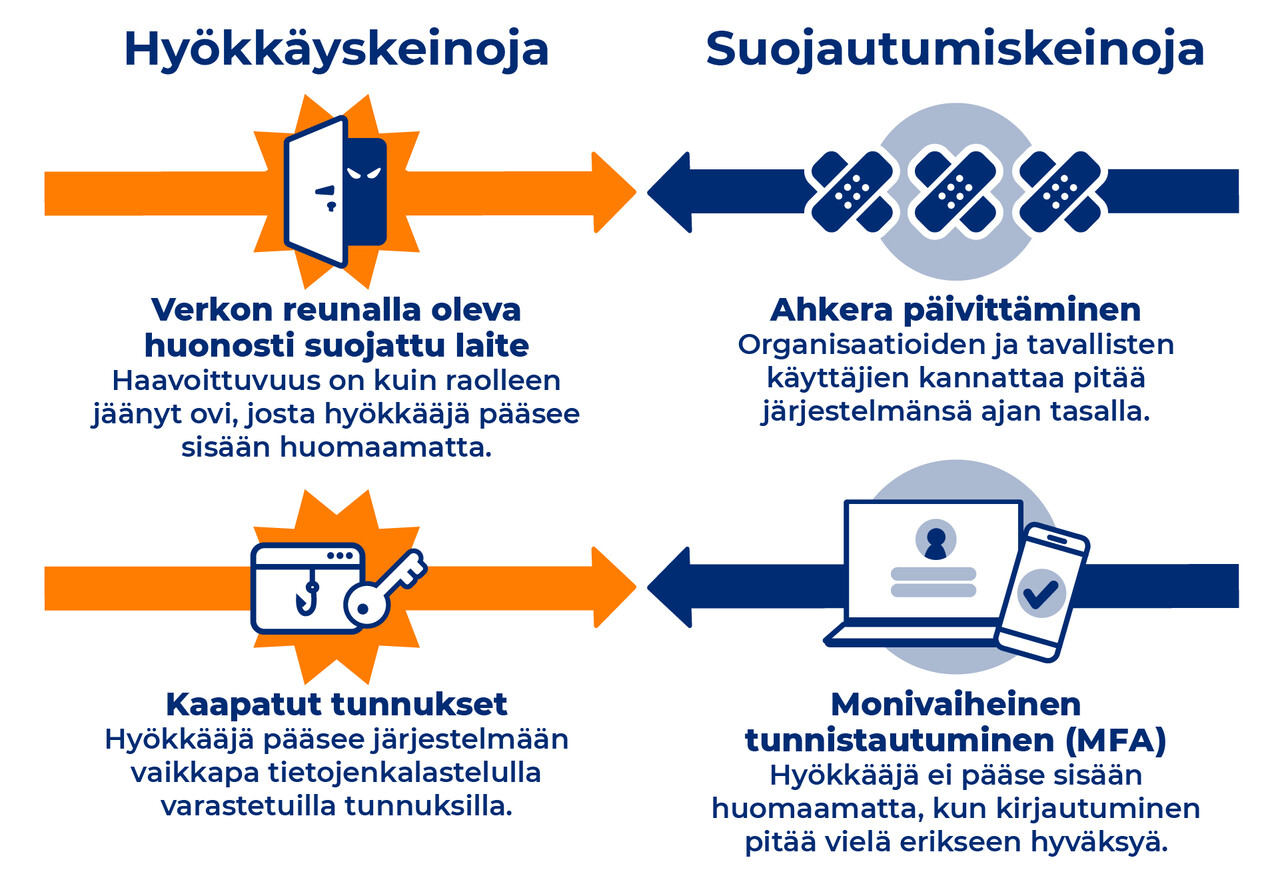
Information security is a thing that you cannot compromise on. Cyber crime is an international activity that poses a threat to all organisations, regardless of their size or sector, with municipalities being no exception. Cyber attacks are almost always motivated by money. Attackers are constantly scouring the internet for poorly protected networks without any regard for the organisations that they belong to, using every means available to them to gain access to that which is most precious to organisations: their data. Stealing data earns the attackers both money and reputation on the criminal market; victims be damned.
When it comes to preparing for and responding to cyber threats, it is also important to keep in mind the importance of active and open communication. Organisations hit by cyber attacks must be able to respond to the information needs of different target audiences without compromising the investigation of the attack. We always urge organisations to communicate openly.
No system is ever 100% secure. Because of this, information security is something that needs to be worked on constantly.
Read more about the importance of information security in our new article here (in Finnish) (External link)
On 2 January 2024, the National Coordination Centre (NCC-FI) of the Finnish Transport and Communications Agency’s NCSC-FI launched an application round aimed at microenterprises and SMEs registered in Finland for financial assistance intended for the deployment of modern cyber security solutions and innovations. The total number of applications received by the deadline of 1 March 2024 was 160. The total amount of financial assistance available was EUR 1.5 million. Based on received applications, financial assistance was granted to 36 companies, with the amounts of assistance granted ranging from EUR 6,622 to 60,000.
The National Coordination Centre has been granted funding under the Digital Europe Programme, which Traficom’s NCSC-FI is allocating to third parties in 2023–2024. The financial assistance is primarily aimed at strengthening companies’ own capabilities and Finland’s national capacity and infrastructure to defend against cyber attacks.
Read more here (in Finnish) (Ulkoinen linkki) (External link).
The United States Cybersecurity and Infrastructure Security Agency (CISA) in partnership with key government, non-government, business and civil society partners has prepared a joint cyber security guide especially for high-risk communities, such as civil society organisations and individuals. The aforementioned partners also included Traficom’s NCSC-FI (article in Finnish)(Ulkoinen linkki). (External link)
The guide provides civil society organisations and individuals with recommended actions and mitigations to reduce the risk of cyber intrusions by state-sponsored threat actors based on detected malicious activity. Additionally, the guide includes recommendations for software manufacturers on how to improve customer security.
Read more about the guide here (in Finnish). (External link)
The Finnish Transport and Communications Agency Traficom in collaboration with the National Emergency Supply Agency is holding the third international hacker event focusing on the cyber security of 5G technology at Dipoli in Otaniemi, Helsinki, on 17–18 May. The event will see information security professionals and ethical hackers work around the clock on challenges posed by event partners. This kind of close cooperation between technology developers and manufacturers, the information security community and public authorities promotes cyber security.
Read more about the event here (External link)
Traficom’s blog on the security of 5G networks (in Finnish) (External link)
When you move to the YouTube website, please note that YouTube has its own cookie and privacy policies.
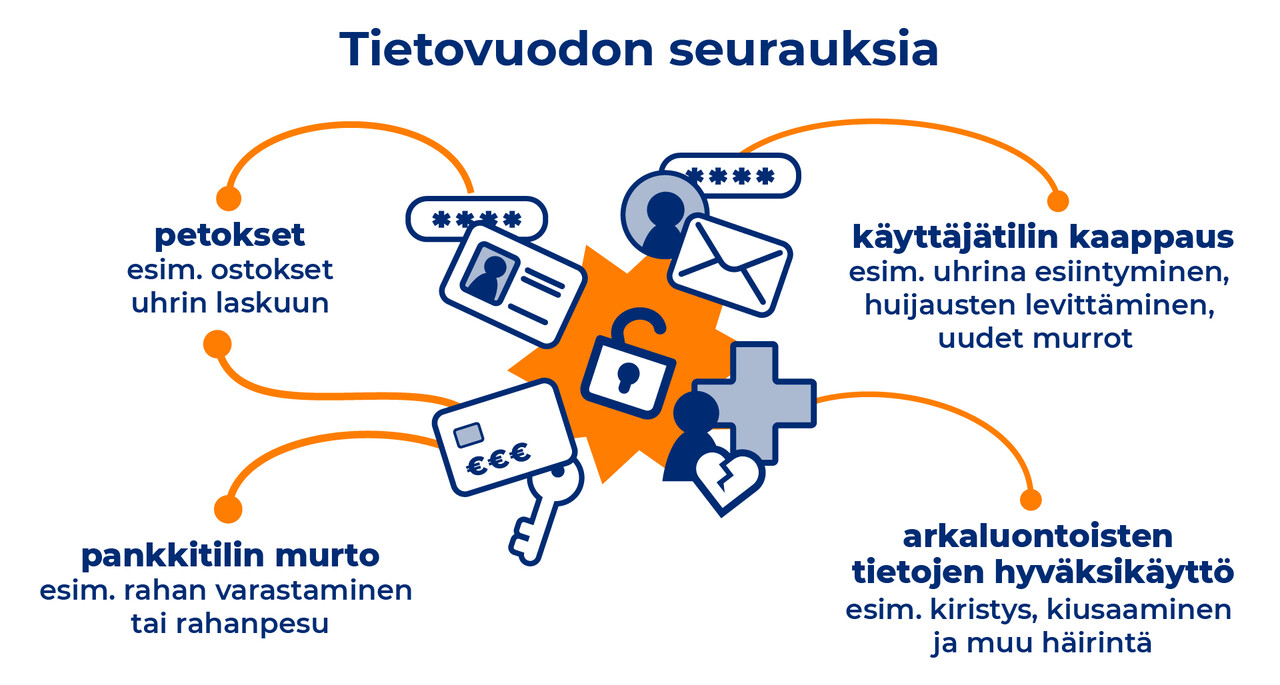
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
CVE: Not defined
CVSS: Several
What: New iOS 17.5 and iPadOS 17.5 versions available for Apple devices
Product: Apple operating systems
Fix: Install the latest updates on your devices
CVE: 10
CVSS: Several
What: SAP released fixes to their products
Products: various SAP products
Fix: Update the products
CVE: Several
CVSS: Several
What: Critical vulnerabilities in Adobe Acrobat and Reader products
Product: Adobe Acrobat & Reader
Fix: Update the products
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 10–16 May 2024). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.